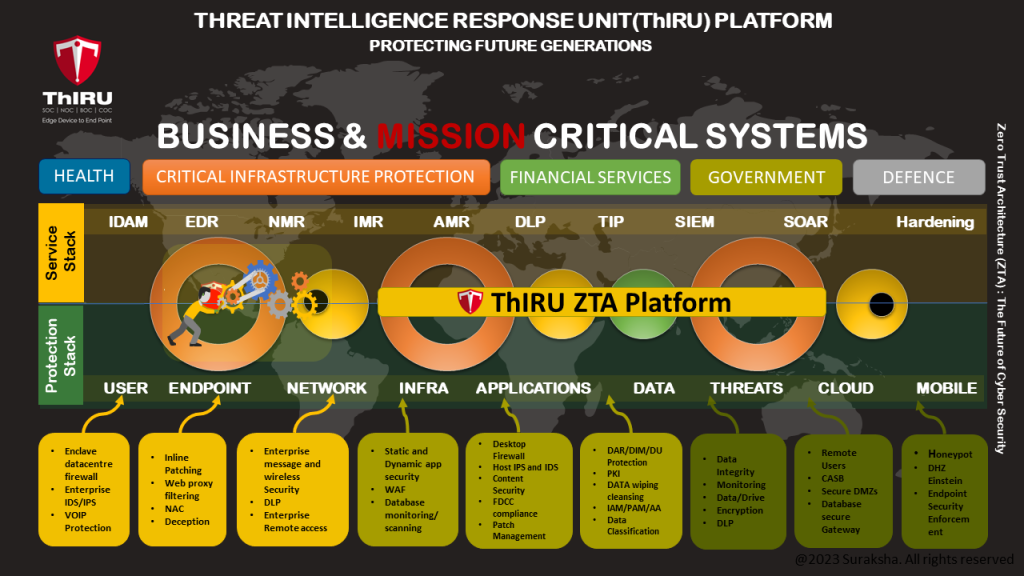
Solutions by Industry

Public Sector
Public sector organizations face increasingly sophisticated cyber threats while often operating with constrained resources. An artificial intelligence-based Security Operations Center (SOC) represents a strategic solution to enhance cybersecurity capabilities while optimizing available resources. This approach leverages advanced technologies to protect critical government infrastructure and sensitive data.
Threat Intelligence and Detection Systems
ThIRU AI-powered continuously monitor network traffic, system logs, and user behavior to identify potential security incidents.
Automated Response Framework
The AI-based SOC implements automated response protocols for
common threat scenarios, enabling rapid containment and mitigation. The system
prioritizes threats based on potential impact to government operations and
critical services.
Compliance Management Systems
Regulatory compliance represents a significant concern for public sector entities. ThIRU can continuously assess systems against relevant frameworks such as FISMA, FedRAMP, CMMC, and jurisdiction-specific requirements.
Data Sovereignty and Security
ThIRU as a Public sector AI-based SOC implementations addresses stringent requirements regarding data location, processing, and access controls.
Benefits and Outcomes
ThIRU AI-based SOC provides public sector organizations with enhanced threat detection capabilities, improved incident response times, and optimized resource allocation Furthermore, the system's ability to learn and adapt ensures ongoing improvement in security posture.
ThIRU is a platform that provides a comprehensive solution for identity management network monitoring infrastructure monitoring data leakage prevention security and incident management including asset and inventory management. The platform is highly scalable and can be integrated into a multi-vendor ecosystem that may already exist. This is a platform for rapid response to cyber warfare.
Education
Educational institutions face a unique cybersecurity
landscape characterized by open networks, diverse user populations, sensitive
research data, and student information protections. An artificial
intelligence-based Security Operations Center (SOC) designed specifically for
the education sector addresses these distinct challenges while accommodating
the resource constraints and operational requirements common to academic
environments. This implementation enhances security capabilities while
supporting the institution's core academic mission and commitment to open
knowledge exchange.
Open Environment Protection
Educational institutions typically maintain relatively open
network environments to facilitate research collaboration and information
sharing. The ThIRU AI-based SOC employs advanced behavioral analytics to
distinguish between legitimate academic activities and potential security
threats without imposing restrictive controls that would impede the learning
environment. Machine learning models develop context-aware security baselines
that account for the varied and sometimes unconventional usage patterns
characteristic of academic networks.
Student Data Safeguards
Educational institutions maintain sensitive student
information subject to various regulations including FERPA in the United States
and similar frameworks globally. The ThIRU AI-based SOC incorporates
specialized monitoring for student information systems, identifying potential
unauthorized access or data exfiltration attempts. The system employs advanced
user behavioral analytics to detect credential compromise or insider threats
that could expose protected educational records.
Research Data Protection
Many institutions conduct sensitive research requiring specialized data protection. The ThIRU AI-based SOC provides tailored monitoring capabilities for research environments, particularly those involving confidential data, intellectual property, or research subject to export controls. Machine learning models identify anomalous access patterns or data transfers that might indicate attempted theft of valuable research assets or regulatory compliance violations.
Budget-Conscious Design
Educational institutions typically operate under significant
budget constraints. The ThIRU AI-based SOC implementation employs
cost-optimization strategies including cloud-based deployment models, tiered
monitoring approaches, and automated response capabilities that reduce staffing
requirements. The system leverages machine learning to prioritize alerts based
on institutional risk factors, focusing limited security resources on the most
significant threats.
Diverse User Community Support
Academic environments encompass diverse user populations
including students, faculty, administrative staff, and guests, each with
distinct usage patterns and access requirements. The ThIRU AI-based SOC
incorporates user context in its security analysis, recognizing legitimate
variations in behavior across different user categories. This approach reduces
false positives from normal academic activities while maintaining effective
threat detection.
Seasonal Operational Patterns
Educational institutions experience distinct operational
cycles with significant variations in network usage and user population across
academic terms. The ThIRU AI-based SOC adapts its baseline expectations and
monitoring parameters to accommodate these cyclical changes. Machine learning
algorithms recognize legitimate seasonal patterns associated with registration
periods, exam weeks, breaks, and research cycles, adjusting detection
thresholds accordingly.
Benefits and Outcomes
An effectively implemented ThIRU AI-based SOC provides
educational institutions with substantially improved security capabilities
despite resource limitations. The system significantly enhances detection of
threats targeting student data, research assets, and institutional systems
without imposing controls that would conflict with academic freedom principles.
Furthermore, the comprehensive monitoring and automated response capabilities
allow institutions to maintain effective security operations with limited
specialized staff.
For educational institutions navigating complex
cybersecurity challenges, an ThIRU AI-based SOC represents a strategic approach that addresses sector-specific requirements while acknowledging common resource constraints. By leveraging advanced technologies with appropriate adaptations for academic environments, these solutions can significantly enhance protection of sensitive institutional data and systems while supporting the organization's core educational mission.

Financial Services
Financial services organizations face unique cybersecurity challenges due to their position as high-value targets for threat actors and their extensive regulatory obligations. An artificial intelligence-based Security Operations Center (SOC)provides comprehensive security monitoring, detection, and response capabilities specifically tailored to the financial sector's requirements. This
approach enhances threat detection accuracy while improving operational efficiency and compliance posture.
Advanced Threat Detection Systems
ThIRU AI-powered detection systems monitor network traffic,
endpoint activities, and user behaviors across the financial organization's
infrastructure. Machine learning algorithms analyze vast quantities of data to
identify anomalous patterns that may indicate compromise.
Financial Fraud Detection Integration
Unlike standard SOC implementations, financial services
require tight integration between cybersecurity operations and fraud detection
systems. ThIRU AI-based SOCs in this sector correlate security events with
transaction anomalies to identify sophisticated attacks that may manifest
across both domains.
Financial institutions must adhere to numerous regulations
including PCI DSS, GLBA, SOX, and jurisdiction-specific requirements. ThIRU AI-based
SOC platforms continuously assess security controls against these frameworks
and generate appropriate documentation for examinations and audits. The system
maintains comprehensive audit trails and evidence collection processes to
demonstrate compliance with regulatory standards to meet Data Privacy
Requirements, Business Continuity
Integration and Third-Party Risk
Management
Benefits and Outcomes
An effectively implemented ThIRU AI-based SOC provides
financial services organizations with substantially improved threat detection
capabilities, particularly for sophisticated attacks designed to evade
traditional security controls Furthermore, the comprehensive monitoring and
documentation capabilities significantly enhance the organization's regulatory
compliance posture.
For financial services organizations facing evolving cybersecurity threats, an ThIRU AI-based SOC represents a strategic investment in security operations capabilities.
Healthcare
Healthcare organizations manage vast amounts of sensitive
patient data while maintaining critical care systems that directly impact human
lives. An artificial intelligence-based Security Operations Center (SOC)
provides specialized cybersecurity monitoring, detection, and response
capabilities designed to address the unique security challenges of the
healthcare sector. This approach enhances protection of sensitive medical
information and clinical systems while supporting regulatory compliance
efforts.
Clinical Systems Monitoring
The ThIRU AI-based SOC incorporates specialized monitoring
capabilities for healthcare-specific systems, including electronic health
record (EHR) platforms, clinical decision support systems, medical devices, and
telehealth infrastructure. Machine learning algorithms analyze activities
across these environments to identify anomalous patterns that may indicate
security compromise. Models receive targeted training on healthcare-specific
attack vectors and normal operational patterns in clinical environments.
Protected Health Information Safeguards
Healthcare SOC implementations feature enhanced capabilities
for monitoring and protecting protected health information (PHI). The system
identifies potential data exfiltration attempts, unauthorized access to patient
records, and suspicious query patterns that might indicate privacy violations.
Machine learning models detect subtle indicators of compromised credentials or
insider threats that could lead to patient data exposure.
Medical Device Security Integration
Unlike traditional SOC implementations, healthcare
organizations require specific capabilities for monitoring connected medical
devices. The ThIRU AI-based SOC incorporates specialized protocols for these
often legacy devices, compensating for their inherent security limitations
through enhanced network monitoring and behavioral analysis. This approach
provides protection for critical care systems that cannot be directly updated
or secured through conventional means.
Regulatory Compliance Framework
Healthcare organizations must demonstrate compliance with
numerous regulations, including HIPAA, HITECH, and regional healthcare data
protection requirements. The ThIRU AI-based SOC continuously assesses security
controls against these frameworks and maintains comprehensive audit trails to
support compliance verification. The system preserves appropriate forensic
evidence while adhering to patient privacy requirements.
Operational Continuity Requirements
Clinical environments cannot tolerate security measures that
impede patient care delivery. The ThIRU AI-based SOC must operate with minimal
performance impact on clinical systems while maintaining rapid response
capabilities. Implementation requires careful coordination with clinical staff
to ensure security operations enhance rather than compromise patient safety and
care quality.
Integration with Existing Healthcare IT Infrastructure
Many healthcare organizations maintain complex technology
ecosystems that include legacy clinical applications, specialized medical
systems, and diverse biomedical devices. The ThIRU AI-based SOC must integrate
effectively with this heterogeneous environment, providing comprehensive
visibility across all systems that interact with patient data or support
clinical operations.
Benefits and Outcomes
An effectively implemented ThIRU AI-based SOC provides
healthcare organizations with substantially improved threat detection
capabilities, particularly for sophisticated attacks targeting patient data or
clinical systems. The system reduces the time required to identify and respond
to security incidents, potentially limiting both care disruption and data
exposure during breach scenarios. Furthermore, the comprehensive monitoring and
documentation capabilities significantly enhance the organization's regulatory
compliance posture.
For healthcare organizations facing evolving cybersecurity threats, an ThIRU AI-based SOC represents a strategic approach to security operations that addresses sector-specific requirements. By leveraging advanced technologies with appropriate clinical environment adaptations, these solutions can significantly enhance protection of sensitive patient information and critical care systems while supporting the organization's core mission of providing safe, effective healthcare services.


Small and Medium Businesses
Small to medium enterprises (SMEs) face many of the same
cybersecurity threats as larger organizations but often lack the resources,
expertise, and infrastructure to implement comprehensive security operations.
An artificial intelligence-based Security Operations Center (SOC) tailored for
SMEs provides enterprise-level security capabilities in a cost-effective,
scalable format appropriate for organizations with limited cybersecurity
resources. This approach democratizes advanced security monitoring and response
capabilities, making them accessible to businesses that cannot support
traditional SOC implementations.
Cloud-Based Security Architecture
The SME-focused ThIRU AI-based SOC leverages cloud-native
architecture to eliminate requirements for extensive on-premises
infrastructure. This approach provides centralized security monitoring across
distributed business environments with minimal deployment complexity. The cloud
implementation enables rapid deployment and ongoing management without
specialized security hardware or substantial IT overhead, making it suitable
for organizations with constrained technical resources.
Automated Threat Response
For SMEs with limited cybersecurity personnel, automated
response capabilities are essential. The ThIRU AI-based SOC incorporates
predefined response playbooks for common threat scenarios, automatically
implementing containment and remediation actions for high-confidence security
incidents. Machine learning algorithms continuously refine these response
mechanisms based on observed outcomes, improving effectiveness while minimizing
disruption to business operations.
Simplified Management Interface
Unlike enterprise SOC implementations that assume specialized security expertise, SME solutions feature intuitive management interfaces designed for general IT personnel. The system presents security information in business-relevant terms, translating technical indicators into actionable intelligence that non-specialists can understand and address. This approach enables effective security management even in organizations without dedicated cybersecurity staff.
Cost Optimization Strategies
SMEs require security solutions with predictable, manageable
costs. The ThIRU AI-based SOC implementation employs various strategies to
control expenses, including tiered service models, shared security
infrastructure, and focused monitoring of critical assets. Machine learning
capabilities optimize resource utilization by prioritizing alerts based on
business impact, reducing false positives that would consume limited response
resources.
Simplified Regulatory Compliance
Many SMEs must demonstrate compliance with various security
frameworks despite limited compliance expertise. The ThIRU AI-based SOC
includes pre-configured compliance templates and automated assessment
capabilities for common requirements such as PCI DSS, GDPR, and
industry-specific regulations. The system generates appropriate documentation
and identifies compliance gaps with remediation guidance, simplifying what can
otherwise be a complex process for resource-constrained organizations.
Integrated Vendor Management
SMEs increasingly rely on third-party services and cloud
applications, creating security dependencies that must be monitored. The ThIRU
AI-based SOC incorporates capabilities to assess and monitor the security
posture of critical vendors and cloud services. This approach provides
visibility into potential supply chain vulnerabilities without requiring
extensive security resources to manually evaluate each provider.
Benefits and Outcomes
An effectively implemented ThIRU AI-based SOC provides SMEs
with security capabilities previously available only to larger enterprises with
dedicated security teams. The system significantly improves threat detection
and response times while reducing the expertise required to maintain effective
security operations. Furthermore, the comprehensive monitoring and
documentation capabilities enhance the organization's ability to demonstrate
security due diligence to customers, partners, and regulators.
For small to medium enterprises facing
increasingly sophisticated cyber threats, an ThIRU AI-based SOC represents a strategic approach to security operations that addresses their specific resource constraints and operational requirements. By leveraging cloud-based architecture, automation, and simplified management interfaces, these solutions can significantly enhance protection of critical business systems and sensitive information while remaining both operationally and financially sustainable. This implementation democratizes advanced security capabilities,Large Enterprise
Core Technology Foundation
ThIRU AI-SOC represents a significant advancement in
security operations center (SOC) technology, built specifically for the complex
security needs of large enterprises. At its foundation lies a multi-layered
artificial intelligence system that combines several AI approaches to create a
comprehensive security monitoring and response capability.
The system employs deep learning neural networks that
continuously analyze network traffic patterns across your enterprise
environment. Unlike traditional signature-based systems that can only identify
known threats, ThIRU AI-SOC 's neural networks develop an understanding of what
constitutes "normal" behavior within your specific organization. This
allows the system to identify subtle anomalies that might indicate a
sophisticated attack, even if the specific attack technique hasn't been seen
before.
Advanced Threat Detection Methodology
ThIRU AI-SOC 's threat detection operates on three
complementary levels, creating a defense mechanism that's difficult for
attackers to circumvent:
First, the system conducts behavioral analysis at the user
level. The AI establishes baseline patterns for each user account within your
enterprise, accounting for role-based variations and even temporal patterns
(like typical working hours or seasonal activities). When a user account
suddenly begins accessing unusual systems or downloading atypical amounts of
data, ThIRU AI-SOC identifies this
deviation even if all formal access policies are being followed.
Second, ThIRU AI-SOC performs network-level analysis, examining the
relationships between systems and data flows. This allows it to detect lateral
movement by attackers who may have compromised one system and are attempting to
expand their foothold. The AI understands the expected communication patterns
between different segments of your network and alerts when unexpected
connections are established.
Third, the system conducts application-level monitoring,
understanding how your critical business applications normally function and
identifying potentially malicious manipulations. This is particularly valuable
for detecting sophisticated attacks that target business logic rather than
technical vulnerabilities.
Enterprise-Scale Data Processing
Large enterprises generate enormous volumes of security
data—often billions of events daily. ThIRU AI-SOC implements a distributed processing
architecture specifically designed to handle this scale without performance
degradation. The system uses advanced data filtering techniques that reduce
noise while preserving security-relevant information.
This distributed architecture allows ThIRU AI-SOC to process security telemetry from tens of
thousands of endpoints simultaneously, correlating events across your entire
infrastructure in near real-time. The system maintains performance even during
security incidents when data volumes may spike dramatically.
Automated Response Orchestration
When ThIRU AI-SOC identifies a security threat, it doesn't
simply generate an alert and wait for human intervention. The system contains a
sophisticated response orchestration engine that can automatically execute
containment and remediation actions appropriate to the specific threat.
For example, if ThIRU AI-SOC detects credential theft activity, it can
automatically trigger account lockdowns and multi-factor authentication
challenges. If it identifies malware propagation, it can isolate affected
systems while preserving forensic evidence. These automated responses occur in
seconds rather than the hours or days that manual intervention often requires.
Each response is calibrated to balance security needs
against business continuity requirements. The system understands which systems
are business-critical and adjusts its response actions accordingly, preventing
disproportionate disruption to your operations.
Integration with Enterprise Security Ecosystem
ThIRU AI-SOC is
designed to enhance rather than replace your existing security investments. The
system includes over 300 pre-built connectors to common enterprise security
tools, allowing bidirectional data flow between ThIRU AI-SOC and your current security stack.
This integration capability means ThIRU AI-SOC can incorporate threat intelligence from your
existing tools while also feeding its advanced analytics back into those
systems. The result is an AI layer that elevates the effectiveness of your
entire security infrastructure rather than creating another isolated security
silo.
Human-AI Collaboration Interface
Despite its advanced automation capabilities, ThIRU AI-SOC recognizes that human security expertise
remains invaluable. The system includes a collaborative interface designed
specifically for security operations teams, presenting information in a way
that augments human decision-making rather than obscuring it.
When security analysts interact with ThIRU AI-SOC , the
system explains its reasoning in clear language, showing not just what threats
it detected but why it classified them as suspicious. This transparency builds
trust between your security team and the AI system, creating an effective
partnership that combines human judgment with computational power.
Continuous Learning and Improvement
Perhaps most importantly, ThIRU AI-SOC continues to evolve its protection
capabilities over time. The system implements a supervised learning approach
where security analysts' responses to alerts are fed back into the AI models,
gradually improving detection accuracy and reducing false positives.
This learning process is specific to your organization,
meaning that ThIRU AI-SOC becomes
increasingly tailored to your particular security needs and environment over
time. Six months after deployment, the system will have developed specialized
knowledge about your infrastructure that generic security tools simply cannot
match.


Defense
Defense organizations operate in uniquely challenging cybersecurity environments where threats extend beyond financial motivations to include nation-state actors, advanced persistent threats, and potential impacts on national security. An artificial intelligence-based Security Operations Center (SOC) provides enhanced capabilities to detect, analyze, and respond to sophisticated cyber threats targeting defense networks, systems, and operations. This specialized implementation addresses the distinct security requirements of military and defense agencies while supporting operational resilience.
Multi-Domain Threat Intelligence
The defense ThIRU AI-based SOC integrates intelligence from
across cyber, physical, and operational domains to develop comprehensive
situational awareness. Advanced machine learning models correlate information
from disparate sources to identify coordinated campaigns that might remain
undetected when viewed through isolated security systems. This capability
enables detection of sophisticated multi-vector attacks designed to compromise
critical defense systems or information.
Classified Environment Support
Defense organizations maintain varying levels of network
classification, from unclassified to highly sensitive environments. The ThIRU
AI-based SOC architecture implements appropriate segmentation and security
controls to support monitoring across these distinct environments while maintaining
proper data separation. Machine learning models receive specialized training
for each classification level, recognizing the unique threat patterns and
operational characteristics present in these environments.
Mission Assurance Focus
Unlike commercial implementations, defense SOCs prioritize
mission assurance above all other considerations. The ThIRU AI capabilities
continuously evaluate potential security incidents in the context of their
impact on critical military functions and operations. This approach ensures
that response activities focus first on maintaining essential capabilities
during cyber incidents, particularly those affecting command and control
systems, weapons platforms, or intelligence assets.
Security Classification Requirements
Defense ThIRU AI-based SOC implementations must adhere to
stringent classification requirements regarding data handling, analysis, and
reporting. Solutions typically require specialized deployment models that maintain
appropriate separation between classification levels while enabling effective
threat monitoring. Implementation includes robust controls for cross-domain
information sharing when operationally necessary.
Supply Chain Security Integration
Defense organizations face significant threats from supply
chain compromises targeting military systems and technologies. The ThIRU AI-based
SOC incorporates specialized capabilities to monitor for indicators of supply
chain infiltration, unauthorized component modifications, or compromised
software dependencies. Machine learning models analyze system behaviors to
identify potential tampering or unauthorized modifications to critical defense
assets.
Autonomous Operation Capabilities
Military networks may operate in disconnected, intermittent,
or limited-bandwidth environments, particularly during deployment scenarios.
The ThIRU AI-based SOC includes capabilities for autonomous operation during
periods of limited connectivity, maintaining effective security monitoring and
prioritized response activities even when central coordination is unavailable.
This resilience ensures continuous protection regardless of operational
conditions.
Benefits and Outcomes
An effectively implemented ThIRU AI-based SOC provides
defense organizations with substantially enhanced capabilities to identify and
respond to advanced cyber threats. The system dramatically improves detection
of sophisticated attack methodologies employed by nation-state actors and other
advanced adversaries. Furthermore, the comprehensive monitoring and rapid
response capabilities significantly enhance operational resilience during cyber
incidents, ensuring the continued availability of mission-critical systems and
information.
For defense organizations facing continuous, sophisticated cyber threats, an ThIRU AI-based SOC represents an essential capability for protecting national security interests. By leveraging advanced technologies with appropriate security controls and defense-specific adaptations, these solutions can significantly enhance protection of critical military systems and sensitive information while supporting the organization's core defense mission.
The implementation provides a force multiplier effect, enabling more effective
utilization of limited cybersecurity personnel while maintaining vigilance
against evolving threat actors.
Critical Infrastructure
T
Critical infrastructure sectors—including energy, water,
transportation, and telecommunications—represent essential systems upon which
modern society depends. These environments face increasingly sophisticated
cyber threats that could potentially disrupt vital services or endanger public
safety. An artificial intelligence-based Security Operations Center (SOC)
provides specialized capabilities to detect, analyze, and respond to threats
targeting operational technology (OT) and industrial control systems (ICS)
while maintaining continuous operations. This implementation addresses the
distinct security requirements of critical infrastructure environments where
availability and integrity are paramount concerns.
OT/IT Convergence Monitoring
The critical infrastructure ThIRU AI-based SOC bridges the
traditional gap between operational technology and information technology
environments. Advanced analytics monitor activity across both domains to
identify threats that may traverse these boundaries. Machine learning models
recognize normal operational patterns within industrial control systems and
detect anomalies that may indicate compromise, even when attacks employ
legitimate commands that would evade traditional security controls.
Physical-Cyber Security Integration
Critical infrastructure protection requires coordinated
monitoring of both cyber and physical security domains. The ThIRU AI-based SOC
correlates information from physical access systems, industrial sensors, and
cybersecurity controls to develop comprehensive situational awareness. This
integration enables detection of sophisticated attacks that may combine
physical access with cyber elements to compromise critical systems or
processes.
Safety-Critical Systems Protection
Unlike conventional IT environments, critical infrastructure systems directly impact physical processes with potential safety implications. The ThIRU AI-based SOC continuously evaluates control system behaviors against established safety parameters to identify potentially dangerous commands or conditions. Machine learning algorithms recognize patterns that could lead to unsafe states, enabling preventive intervention before safety thresholds are breached.
Operational Continuity Requirements
Critical infrastructure environments cannot tolerate
security measures that interrupt essential services. The ThIRU AI-based SOC
must operate with minimal performance impact on industrial systems while maintaining
effective monitoring capabilities.
IT: Information Technology
ThIRU Cyber Security Platform provides robust, comprehensive IT protection, ensuring data security, threat mitigation, and operational resilience for organizations.
OT: Operational Technology
ThIRU Cyber Security Platform offers advanced OT protection, enhancing operational security, risk management, and resilience in critical infrastructure environments.

Focused Solutions